A Shift in Australia’s Threat Landscape
The terrorist incident occurring on December 14, 2025, during the “Chanukah by the Sea” event at Archer Park, Bondi, represents a profound shift in the Australian domestic threat landscape. The multi-modal attack that was characterised by the tactical exploitation of elevated urban high ground, resulted in 15 fatalities and over 40 injuries (Doherty et al., 2025).
December in Australia marks the official commencement of summer and the onset of the holiday season. With schools winding down and offices in party-mode, the community changes down a gear and the festivities merge with Australia’s beach culture; a phenomenon that is no more manifest than at Sydney’s Bondi beach. The horrific attack on 14 December 2025 targeted the Jewish community, but it was an attack on Australia, an attack on us all.
Chanuka by the Sea is a quintessential Australian event, where ancient Judaic rituals and symbolism play out on the iconic Bondi Beach. In 2025, it was an open-air event at the northern end of the beach in a triangular section called Archer Park, as shown in Figure 1. There are access roads around the area and a heritage pedestrian bridge with an elevation of 15m and clear line of sight into the park. The attackers would use this to horrific effect.

Figure 1. Chanuka by the sea - Archer Park. Lote graphic. Image: Google Earth.
How the Bondi Attack Unfolded
The attack began at approximately 6:45 pm and finished at 6:50 pm when NSW Police forces neutralised the attackers (Doherty et al., 2025). The attackers parked their vehicle 15 metres from the pedestrian bridge, moved into position, lobbed improvised explosive devices into the crowd in the form of tennis balls and pipe bombs (Bogle, 2025), took up positions with their high-powered long arm rifles on the bridge and began shooting into the crowd.
The police responded and exchanged fire with the attackers, eventually killing one and injuring the other, at which point he was apprehended. Significantly, the attack was captured from adjoining buildings and from an overhead drone. A Royal Commission is currently active to investigate all circumstances surrounding the events of the terror attack. The following are lessons drawing upon what we currently know.
Security Vulnerabilities Exposed
While event organisers established a security perimeter, considered and mitigated hostile vehicle threats and carried out bag searches, the attackers operated from outside the security perimeter by capitalising on the height of the bridge, the line of sight into the crowd and the long range of their firearms. The elevation of the bridge gave the attackers a defensible vantage point, since the heritage bricks provided them with a level of ballistic protection.
The families congregated at the event were thrown into an impossible situation. The onset of the attack may have initially sounded like fireworks, but that soon materialised into a horrific reality of gunmen firing into the crowd. Panic would have come quickly and the crowd either could have frozen, taken cover or run. Many inadvertently ran into the line of fire.
Venues hosting special events present complex security challenges as crowded places. Despite a PROBABLE rating on the National Terrorism Threat Level, where there is more than a fifty percent likelihood that an attack or the planning of an attack could occur within the next twelve months, the likely attack vectors were hostile vehicles or handheld weapons such as the knife attack at the Bondi Westfields a year earlier. An armed attack of this scale was neither anticipated, nor prepared for.
Hindsight means that we must now anticipate, prepare and mitigate such horrific risks, even in Australia. While we often wrongly assume that gun violence is a very US-centric occurrence, Port Arthur, Christchurch and now Bondi are wake up calls to take such risks very seriously.
Protecting special event venues means conducting thorough site security audits. Considering not just the two-dimensional security perimeter but a three-dimensional spherical perimeter centred on the event venue. Red team thinking, where security professionals think of how an attacker might carry out their attack, is used to find and secure any vantage points, with sight lines and access. These areas that are outside the venue’s control but impact or are impacted by the event are often defined as Grey Space or Zone Ex (NPSA, 2024, p.7).
These site audits must be carried out in the lead up to the events and all targeting locations scoped out and secured for the duration of the event. This can be achieved through a combination of access control, security patrols and coordination with Local Council and Police. Temporary mobile video surveillance solutions can also be used to supplement the situational awareness of the security team on the day. Additional security measures such as ballistic blankets, visual occlusion screens, and even drone nets can be deployed to provide addition protection to the crowd.
Crucially, it falls upon the event organisers and the contracted security team to conduct pre-event venue sweeps; white level searches through the three-dimensional security perimeter to detect suspicious objects, vehicles, equipment and people. Relying on security contractors mean that special event organisers need to have a very clear security plan for the event based on a security risk management framework as prescribed in HB 167: 2025. Additionally, having clear and succinct security protocols and lines of responsibility and reporting are critical to the efficacy of the event day security operation. The effectiveness of the security team in an emergency is proportionate to the highest level of their training and practice, and the skill base each individual brings in terms of communication and experience in hostile environments.
The role of the security team is to deter and/or detect the threat, delay the attack, alert the Police and to direct the crowd on how to respond. The Australian government’s guidance to “Run, Hide, Tell” (ANZCTC, 2023, p.5) in the event of an attack needs to be enacted on scale by a crowd that also includes the disabled, children and the elderly. Every special event venue must have designated safe zones where the crowd instinctively knows to go in the event of an attack. Communication of this to event attendees must take on the same rigour and simplicity as the safety briefing on an airline. Crucially, the event organisers must have a multi-faceted communication strategy including the use of PA systems, WhatsApp groups or other social media broadcasts. This should be documented in the Communication plan.
In crowd management contexts, responses to dangerous situations can be highly unpredictable, with some individuals freezing or looking away while others are more inclined to take action. As a result, it is critical that individuals are educated on how to recognise suspicious behaviour and respond appropriately under such conditions. Computer-based modelling of crowd scenarios can be used to identify areas of concern, enabling targeted interventions that strategically enhance safety and increase the likelihood of survival in emergency situations (Haghani, 2025). Haghani identified three key behavioural strategies in violent attacks. These include moving away from threats quickly, to prevent hesitation, and to monitor surroundings and allow for agile decision-making (Haghani, 2025).
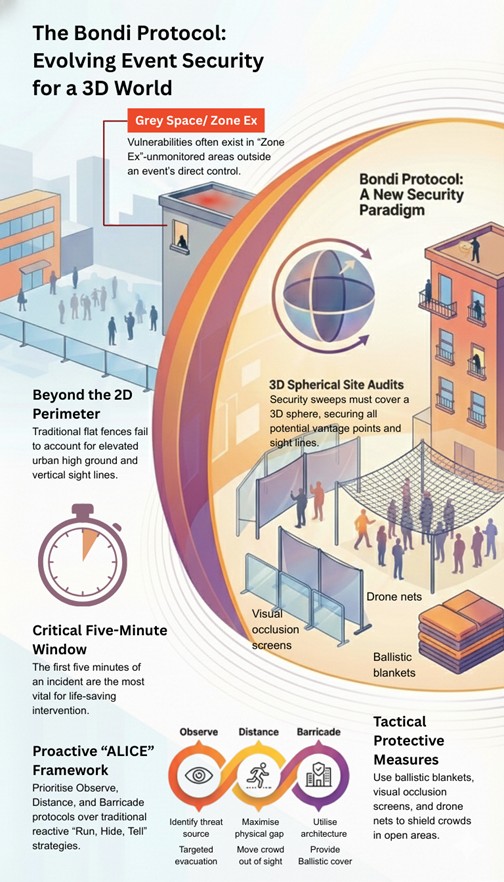
Figure 2. The Bondi Protocol
From Run Hide Tell to the Bondi Protocol
The Bondi attack demonstrates that during an active shooter incident, the first five minutes are critical. The “Run, Hide, Tell” (ANZCTC, 2023, p.5) falls short in providing clear guidance for how event organisers and security staff can manage the crowd.
An alternative framework is ALICE, which stands for Alert, Lockdown, Inform, Counter, and Evacuate. It is a commonly implemented set of protocols followed in various US sectors including government, law enforcement and schools (ALICE Training, 2026). Under this protocol, three main security protocols consisting of “Observe, Distance, Barricade” can be followed upon the discovery of an armed attack. The first step is to observe and identify, which in the case of the Bondi attack would have been to identify the source of the gunfire. At this point a PA announcement could have instructed the crowd that there is an attack from the North footbridge and to evacuate to the South towards the Pavilion. The second step ‘lockdown’ is to maximise distance between the crowd and the shooter by moving the crowd away from the line of sight, and where possible use physical structures such as the concrete architecture of the Bondi Pavilion or the sea wall as ballistic cover. In this step, lockdown procedures would be followed where possible with entry points barricaded, locking doors, turning off lights, and silencing all communication devices. This protocol provides a more proactive approach for event organisers and security staff. The next step would be to share timely information with those in danger is possible to aid in guiding decision-making and support coordinated crowd movement. The counter element is considered a last resort due to the significant risk to life and is intended solely to disrupt an attacker’s ability to cause harm and create opportunities for escape. This was demonstrated during the Bondi attack through the courageous actions of a bystander, who intervened to disarm one of the attackers, preventing further loss of life under already critical circumstances. The final step is to evacuate when it is safe to do so, increasing distance from the immediate threat area. Overall, the ALICE framework offers event organisers and security personnel a structured yet adaptive approach to managing armed attack scenarios, prioritising rapid decision-making, situational awareness, and life safety.
Conclusion
The tragedy of the Bondi terrorist attack on 14 December 2025 serves as a case study in the evolution of urban terrorism. By utilising unmonitored “Grey Spaces” the assailants were able to exploit topographical characteristics of the site to their tactical advantage. While the failure of the attackers IEDs and the heroism of the public saved many lives, future security plans need to be significantly upgraded to mitigate this threat.
The Bondi Protocol shifts the security paradigm from a two-dimensional perimeter or fence mentality to a three-dimensional overwatch, with security risk management practices, site security audits, risk control plans and robust event-specific security plans prepared well in advance. Crucially, the Bondi Protocol calls on event organisers to establish safe zones, train their staff and security contractors, conduct drills and establish communication plans that be deployed in an emergency to save lives. Incorporating proactive frameworks such as Observe, Distance and Barricade from the ALICE framework, rather than reactive ones like Run, Hide, and Tell can also help.
References
- ALICE Training. (2026). ALICE Training®: the original civilian active shooter response training your organization needs. Alice a Solution of Navigate 360. https://www.alicetraining.com/training/
- Australia–New Zealand Counter-Terrorism Committee. (2023). Australia’s Strategy for Protecting Crowded Places from Terrorism. In www.nationalsecurity.gov.au (pp. 1–18). ANZCTC. https://www.nationalsecurity.gov.au/protect-your-business/crowded-places/australias-strategy-for-protecting-crowded-places
- Bogle, A. (2025, December 22). Police allege Bondi shooters had “tennis ball bomb” and made IS-inspired video manifesto, court documents reveal. The Guardian; The Guardian. https://www.theguardian.com/australia-news/2025/dec/22/police-alleged-bondi-shooters-had-tennis-ball-bomb-and-video-manifesto-linked-to-is-court-documents-reveal-ntwnfb
- Doherty, B., Evenshed, N., & Shimada, Y. (2025, December 15). Visual explainer: How a night of terror unfolded in Bondi. The Guardian. https://www.theguardian.com/australia-news/2025/dec/15/a-visual-guide-to-the-bondi-beach-terror-attack
- Haghani, M. (2025, December 15). Intervene or run and hide: what should you do during public violence like the attacks at Bondi? The Conversation. https://doi.org/10.64628/aa.5y6mgvgqf
- National Protective Security Authority. (2024). Mitigation of Terrorist Threats at Venues during Ingress and Egress Guidances. In www.npsa.gov.uk (pp. 1–31). NPSA. https://www.npsa.gov.uk/emergency-incident-management/marauding-terrorist-attacks-mta/mitigation-terrorist-threats-venues-during-ingress-and-egress-guidance
